KRACK: The Massive Wi-Fi Security Flaw
The biggest Wi-Fi security flaw had just been exposed – affecting a large portion of internet connected devices and especially dangerous on more modern devices. To put it simply, your devices such as desktops, laptops, routers, smart TVs, tablets, e-readers, printers or any other smart home devices which uses Wi-Fi for internet connectivity are vulnerable to this flaw.
Discovered by Belgian security researcher Mathy Vanhoef of imec-DistriNet, the aptly dubbed KRACK (Key Reinstallation Attack) exploits a serious weakness in WPA2 – a widely used protocol that secures all modern protected Wi-Fi networks. The research papers will be presented by Vanhoef himself at the Computer and Communications Security (CCS) F3 Session on November 1 entitled “Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2”
How KRACK Exploits WPA2
KRACK targets a vulnerability in the 4-way handshake of the WPA2 protocol. Usually, this handshake is executed when a user wants to join a protected Wi-Fi network. To put it briefly, when a client joins a network – it executes the 4-way handshake which negotiates a fresh encryption key. The key will then be installed after receiving “step 3” of the 4-way handshake and will later be used to encrypt the normal data once the connection is established. In other words, it’s used to confirm that both the client and access point has the correct credentials before allowing a connection.
However, since messages may be lost or dropped throughout the handshake process, the access point will retransmit “step 3” if it did not receive the appropriate response. Hence, the client may receive “step 3” multiple times which then reinstalls the same encryption key again and therefore resets the incremental transmit packet number (nonce) – the starting point of the whole exploit.
Using KRACK, Vanhoef was able to show that an attacker can force these nonce resets by collecting and replaying retransmissions of “step 3” of the 4-way handshake. By doing so, an opportunistic hacker could maliciously intersect the packets that are being transmitted.
Currently, all modern protected Wi-Fi networks use the 4-way handshake which means the attack could also work on older protocols such as WPA or even just AES.
67% Of Internet Connected Devices Worldwide At Risk
It’s absolutely vital that manufacturers quickly deploy patches and that consumers are well aware of the situation!
– As recorded by Wigle
What Are The Impacts
Perhaps the most frightening aspect of this vulnerability – an attacker may leverage it to conduct attacks such as data packet decryption and injection, TCP connection hijacking, HTTP content injection, or the replay of unicast, broadcast, and multi cast frames.
The video below created by Vanhoef demonstrates an attack against an Android smartphone. In this demonstration, you can see the types of information that an attacker could obtain which are not limited to just revealing login credentials – but any data or information the victim transmits can be decrypted.
KRACK attack proof of concept against Android and Linux credits by Mathy Vanhoef
Although the demonstration may seem to portray a quick and easy hack, this is only because the attack is especially catastrophic against version 2.4 and above of the wpa_supplicant – a popular Wi-Fi client which is used on Linux and Android versions 6.0 and above.
Android Devices Worldwide Are Worst Affected
Android versions 6.0 and above covers about 50% of all Android users and is especially prominent on newer devices. This gravely puts a large portion of internet users in exceptional vulnerable situations to this attack.
Google says the company is “aware of the issue, and we will be patching any affected devices in the coming weeks.”
– As recorded by Google
What Systems Are Affected
The bad news – This affects every device that uses Wi-Fi.
The good news – It is fixable through a software update (unless your device is too old for an update patch in which case a hardware replacement is required)
Here’s a quick list of some of your devices that needs the critical update when it’s released, including:
● Desktop computers
● Laptop computers
● Mobile phones
● Tablets
● E-readers (uses Wi-Fi)
● Internet Routers (home and office)
● Smart Home devices (i.e. NEST, Amazon Echo, Google Home, etc.)
● Printers (uses Wi-Fi)
● Any other devices that uses Wi-Fi
If Your Device Supports Wi-Fi
Then it’s almost certain that you’re affected by this vulnerability.
– As reported by Wordfence
Where Is The Fix/Patch
Microsoft was one of the first large company’s that released a security update on the 10th of October so customers who have Windows Update enabled and applied the update are protected automatically. As reported by Microsoft, “We updated quickly to protect customers as soon as possible, but as a responsible industry partner and to protect customers also using other platforms, we withheld disclosure until other vendors could develop and release their own updates.”
Meanwhile, Apple has already patched the vulnerability in the developer and public betas for iOS, macOS, watchOS and tvOS. As reported by iMore, “Apple is deeply committed to protecting our customers’ data. The fix for the KRACK WiFi vulnerability is currently in the betas of iOS, macOS, watchOS and tvOS and will soon be rolled out to customers.”
For a full list of vendors with their patches and further information, BleepingComputer is maintaining a collective database at the link below:
List of Firmware & Driver Updates for KRACK WPA2 Vulnerability by BleepingComputer
To stay up-to-date with official information from US-CERT, you may visit their website using the link below:
Wi-Fi Protected Access (WPA) handshake traffic can be manipulated to induce nonce and session key reuse by US-CERT
How Do I Stay Safe
With the vulnerability exposure only barely a week old, it’s very likely that updates will only start being pushed out in the coming weeks. This means that there probably won’t be an instant fix any time soon so you need to take extra precautions until those become available.
Here are some recommended tips to keep yourself safe:
● Avoid using Wi-Fi. Since the vulnerability targets your device’s Wi-Fi, the best thing to do is to stop using Wi-Fi altogether. You could use a wired ethernet connection instead or just stick to your cellular connection on your mobile.
● Avoid Public Wi-Fi. If you have no choice, we recommend you to only visit websites that use the “HTTPS” standard. This can be identified by the “lock” symbol in the website’s URL or by simply ensuring that the website URL starts with “HTTPS” instead of “HTTP”.
● Use a trusted VPN. Since VPNs will encrypt all of your connection data using another set of encryption methods, it’ll make it much harder to decrypt any of your data even if you’re being attacked by KRACK.
Don’t Have a VPN yet? give our Free Trial a go by clicking the button below for 3 full days of unlimited access to both our VPN and MyTelly services.
I’m sure you’ve got plenty of questions in regards to the KRACK vulnerability. We’ve compiled and expanded some of the most relevant answers by Vanhoef himself below:
Do we now need WPA3?
No, luckily implementations can be patched in a backwards-compatible manner. This means a patched client can still communicate with an unpatched access point (AP), and vice versa. In other words, a patched client or access point sends exactly the same handshake messages as before, and at exactly the same moment in time. However, the security updates will assure a key is only installed once, preventing our attack. So again, update all your devices once security updates are available. Finally, although an unpatched client can still connect to a patched AP, and vice versa, both the client and AP must be patched to defend against all attacks!
Should I change my Wi-Fi password?
Changing the password of your Wi-Fi network does not prevent (or mitigate) the attack. So you do not have to update the password of your Wi-Fi network. Instead, you should make sure all your devices are updated, and you should also update the firmware of your router. Nevertheless, after updating both your client devices and your router, it’s never a bad idea to change the Wi-Fi password.
What if there are no security updates for my router?
KRACK’s main attack is against the 4-way handshake, and does not exploit access points, but instead targets clients. So it might be that your router does not require security updates. Vanhoef strongly advise you to contact your vendor for more details. In general though, you can try to mitigate attacks against routers and access points by disabling client functionality (which is for example used in repeater modes) and disabling 802.11r (fast roaming). For ordinary home users, your priority should be updating clients such as laptops and smartphones.
The 4-way handshake was mathematically proven as secure. How is the KRACK attack possible?
The brief answer is that the formal proof does not assure a key is installed once. Instead, it only assures the negotiated key remains secret, and that handshake messages cannot be forged.
The longer answer is mentioned in the introduction of Vanhoef’s research paper: the attacks do not violate the security properties proven in formal analysis of the 4-way handshake. In particular, these proofs state that the negotiated encryption key remains private, and that the identity of both the client and Access Point (AP) is confirmed. Our attacks do not leak the encryption key. Additionally, although normal data frames can be forged if TKIP or GCMP is used, an attacker cannot forge handshake messages and hence cannot impersonate the client or AP during handshakes. Therefore, the properties that were proven in formal analysis of the 4-way handshake remain true. However, the problem is that the proofs do not model key installation. Put differently, the formal models did not define when a negotiated key should be installed. In practice, this means the same key can be installed multiple times, thereby resetting nonces and replay counters used by the encryption protocol (e.g. by WPA-TKIP or AES-CCMP).
Should I temporarily use WEP until my devices are patched?
NO! Keep using WPA2. WEP is considered the lowest and oldest encryption standard for Wi-Fi security, so you should avoid it. Here’s a quick comparison chart below for an easier overview of Wi-Fi encryption standards.
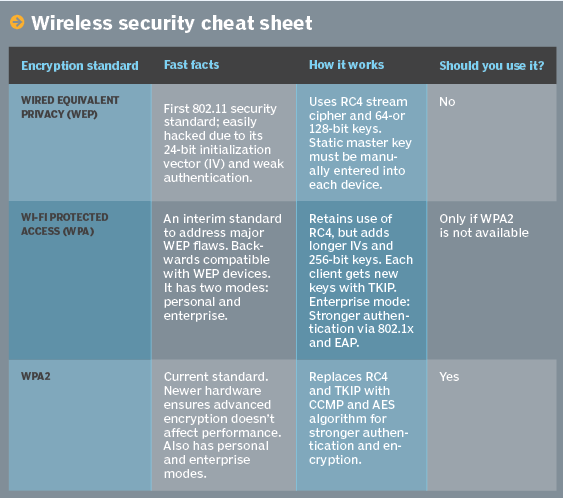
– Image credits by TechTarget’s SearchNetworking.com
For the full list of Q&A and further information regarding the KRACK attack, we recommend you to visit Vanhoef’s official KRACK website at www.krackattacks.com.
We hope you found this article informative or useful. Help us get the word out and bring more awareness by sharing this with your friends and family!
If you need any help regarding our VPN services, we’re just an email away at [email protected]. Shoot us an email and our support team will try their best to help you out.