NotPetya Ransomware Attack | What is it and how to prevent it

First discovered in 2016, the NotPetya malware which had resurfaced on 27 June, 2017 got some experts identifying NotPetya as a cyberattack rather than the usual ransomware. Many of you might remember the last major ransomware attack ‘WannaCry’ that hit the web on 12 May, 2017 had greatly paralysed Britain’s National Health Service (NHS) and also affected more than 230,000 computers in over 150 countries. Like WannaCry, NotPetya spread rapidly through networks that use Microsoft Windows by exploiting the same EternalBlue vulnerability. However, this is a new variant of NotPetya which also uses a second exploit by targeting the EternalRomance vulnerability. These two exploits has since been fixed in security update MS17-010 by Microsoft on March 14, 2017.
Who Has Been Infected
Utilising this new variant of NotPetya, hackers were able to infect more than 80 companies with the majority of them being in the Ukraine according to cybersecurity company Group-IB. At the same time, Microsoft has also estimated over 12,000 infected machines and security firm McAfee has stated that the malware has spread across the U.S., large parts of Europe, South America, and large Asian countries too.
Infected Ground Zero
Security researchers and Ukraine’s cyber police seem to be pointing fingers at MeDoc, an accounting software used by many industries in Ukraine. MeDoc pushed out an update which was then compromised by the hackers and allowed the computer networks to get this malware.
How Do I Know If I’m Infected
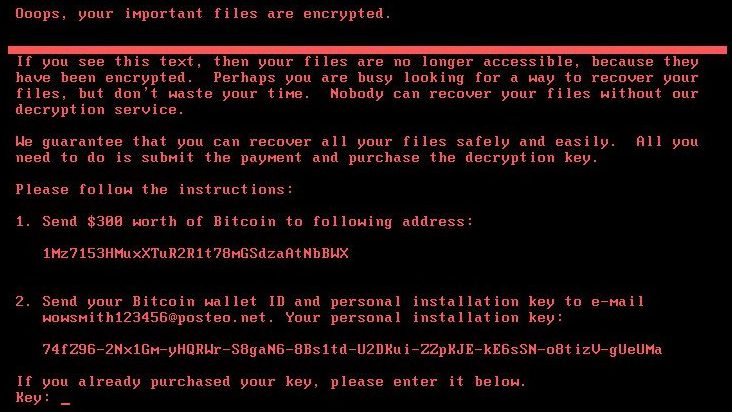
Firstly, NotPetya works by encrypting most or all of the files on your computer. It then demands that a ransom of $300 (£230) be paid in bitcoin to unlock the files.
Having said that, it seems that a new update from researchers are indicating that the email associated with the hackers has been decommissioned, meaning if you pay, there is no way to contact the criminals. In addition to that, Kaspersky Lab has revealed that this new NotPetya variant is in fact a wiper, which means that there’s no possible way to recover the encrypted files as the key is not preserved and given to the user to request a decryption key.
NotPetya Ransom Payment Prompt – you’ll see this screen if you’re infected.
Which Windows Systems Are Affected?
Any Microsoft Windows systems that are not up to date. See the full list below.
● Windows 10 (1507,1511,1607)
● Windows 8/8.1
● Windows 7
● Windows Vista
● Windows XP
● Windows Server 2008, 2008 R2, 2012, 2012 R2
How To Protect Myself From NotPetya
It’s very important that you keep your system updated to avoid the risk of being infected.
Follow the steps below and download the latest patch from the official Microsoft Windows library.
Check Your Windows Version
Kindly follow the steps below to check the version of windows you’re running.
1) Press the Windows key + R on your keyboard.
2) In the Run box that appears, type winver and click OK.
3) A windows showing your Windows version will open.
4) Take note of the Windows version and look for the appropriate Windows solution below.
For Windows 10
1) Search and open your Settings.
2) Click on Update and Security.
3) Click the Windows Update tab and it should show you any available updates. If it’s not showing, you can check for the latest update by clicking on Check for Updates.
4) Click Download to start the update process.
For Windows 8
No update available for this version. Kindly upgrade to Windows 8.1.
Temporary Fix: The steps below is to block the vulnerable SMB protocol.
Warning: Blocking the SMB protocol will remove functionality for file sharing, printing over a network, and others. Read more on how SMB protocols are used here.
1) On the Start screen, type PowerShell.
2) Right-click the Windows PowerShell app icon and select Run as administrator.
3) Once PowerShell is launched, type powershell and hit enter.
4) Type or copy/paste the commands below to PowerShell and hit enter after every command,
Press Y and hit Enter when prompted.
Press Y and hit Enter when prompted.
5) Reboot your computer after it’s successful.
For Windows 8.1
Download Windows 8.1 64-bit NotPetya Patch Fix (KB4019215) Here
Download Windows 8.1 32-bit NotPetya Patch Fix (KB4019215) Here
For Windows 7
Download Windows 7 64-bit NotPetya Patch Fix (KB4019264) Here
Download Windows 7 32-bit NotPetya Patch Fix (KB4019264) Here
For Windows Vista
Download Windows Vista 64-bit NotPetya Patch Fix (KB4012598) Here
Download Windows Vista 32-bit NotPetya Patch Fix (KB4012598) Here
For Windows XP
Download Windows XP SP2 64-bit NotPetya Patch Fix (KB4012598) Here
Download Windows XP SP3 32-bit NotPetya Patch Fix (KB4012598) Here
For Windows Server 2008
Download Windows Server 2008 Itanium NotPetya Patch Fix (KB4012598) Here
Download Windows Server 2008 64-bit NotPetya Patch Fix (KB4012598) Here
Download Windows Server 2008 32-bit NotPetya Patch Fix (KB4012598) Here
For Windows Server 2008 R2
Download Windows Server 2008 R2 Itanium NotPetya Patch Fix (KB4012215) Here
Download Windows Server 2008 R2 64-bit NotPetya Patch Fix (KB4012215) Here
For Windows Server 2012
Download Windows Server 2012 64-bit NotPetya Patch Fix (KB4012217) Here
For Windows Server 2012 R2
Download Windows Server 2012 64-bit NotPetya Patch Fix (KB4012216) Here
For the full list of Windows patches available for the NotPetya Ransomware (MS17-010), kindly visit the Microsoft library here.
I’m infected with NotPetya. What Can I Do?
When a computer is initially infected by the ransomware, it will wait for about an hour before rebooting the machine. While the machine is rebooting, you can switch the computer off which should prevent the files from being encrypted and give you a little more room to try and rescue the files, as flagged by @HackerFantastic on Twitter.
If machine reboots and you see this message, power off immediately! This is the encryption process. If you do not power on, files are fine. pic.twitter.com/IqwzWdlrX6
— Hacker Fantastic (@hackerfantastic) June 27, 2017
However, if you already have a backup of your data or system, you’re in luck. So far the only sure way to remove the ransomware is to,
● Reformat your computer and restore a previously uninfected version of it; OR
● Install a new Windows OS and restore the data files you have backed up.
Should I Pay The Ransom?
We at My Private Network, strongly suggest that you DO NOT adhere to their demands. As reported by The Guardian, cybersecurity experts have warned affected users against meeting the hackers’ demands for money. Also as mentioned above, the ransomware is a wiper with no possibility of data recovery once payment is made.
How To Avoid Ransomware?
There’s a very important lesson to learn from all of this, and that’s to always keep your devices up to date and never jailbreak/root your device.
We hope you found this article informative or useful. Help us get the word out and stop the spread of the ransomware by sharing this with your friends and family!